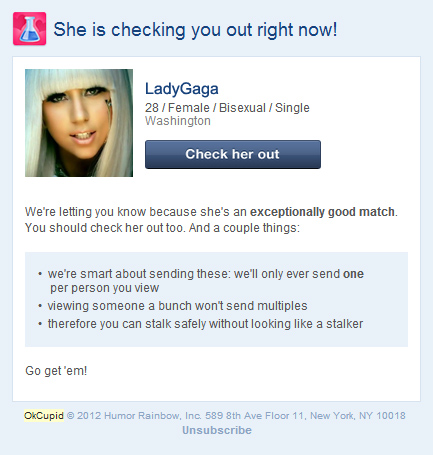
I like Ellen DeGeneres. Lots of people respect what she does and she has a reputation of treating people right. However, I was surprised when I came across a clip from her popular daytime television show where she unsuspectingly broadcasts compromising Facebook photos of random audience members, a sketch I saw for the first time yesterday, and there seems to be at least a few more of these on YouTube.
I get it, it’s a gag on context collapse: photos taken in and for one time and place are dislocated onto broadcast television, to unexpected and hilarious results. Cute. However, the reality of this is not so funny, and The Ellen DeGeneres Show should know better.
The problem here is that Ellen is setting a precedent that it is okay and fun to share each others information to a larger audience than was initially intended; that blasting compromising photos from someone’s Facebook profile to other audiences, large or small, is a funny joke. For many, it isn’t.
Ellen’s lighthearted joke takes the form of much modern bullying; especially what is often called “cyberbullying” more...


 Experiencing global events through social media has become increasingly common. For those in the West, the uprisings over the past few years in the Middle East, North Africa and elsewhere were especially striking because social media filled an information void created by the lack of traditional journalists to cover the dramatic events. By simply following a hashtag on Twitter, we tuned into those on the scene, shouting messages of revolution, hope, despair, carnage, persistence, misinformation, debate, sadness, terror, shock, togetherness; text and photos bring us seemingly closer to the events themselves.
Experiencing global events through social media has become increasingly common. For those in the West, the uprisings over the past few years in the Middle East, North Africa and elsewhere were especially striking because social media filled an information void created by the lack of traditional journalists to cover the dramatic events. By simply following a hashtag on Twitter, we tuned into those on the scene, shouting messages of revolution, hope, despair, carnage, persistence, misinformation, debate, sadness, terror, shock, togetherness; text and photos bring us seemingly closer to the events themselves.