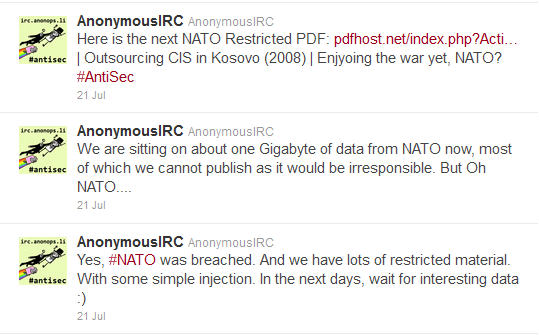
Hacking is the new social justice activism, and the Panama Papers are the result of an epic hack. Consisting of 11.5million files and 2.6TB of data, the body of content given to German newspaper Süddeutsche Zeitung by an anonymous[1] source and then analyzed by the International Consortium of Investigative Journalists (ICIJ), is uniquely behemoth. It puts Wikileaks 1.7GB to shame.
The documents were obtained from Mossack Fonseca. The company is among the largest offshore banking firms, and their emails and other electronic documents tell a compelling (if not entirely surprising) story about untraceable monetary exchanges and the ways that state leaders manage to grow their wealth while maintaining a façade of economic neutrality. By forming shell companies, people can move money without attaching that money to themselves. This is not a sufficient condition for illegal activities, but certainly fosters illicit ones. more...