If you live in the United States and have been adjacent to something with the news on it, you have probably heard of the “Fiscal Cliff.” The fiscal cliff refers to several major tax breaks and earned benefit compensation programs that were set to expire at the end of 2012 unless Congress raised the debt ceiling. One of the few good things to come out of this manufactured crisis was some excellent reporting on the power of metaphor in politics. The ability to spur action and drive public opinion while offering next-to-no information demonstrates the awesome power of metaphors. Most people did not know why we were falling off the cliff, what the cliff was made of, or what the consequences for falling would be. Slate’s Lexicon Valley covered this phenomenon in an episode last month titled “Good is Up.” Co-hosts Mike Vuolo and Bob Garfield dissected the cliff metaphor using the classic book, Metaphors We Live By (1980) by George Lakoff and Mark Johnson. Vuolo and Garfield note, “‘Success is rising’ and ‘failing is falling.’ Lakoff believes these primal, spatial metaphors form what he calls a ‘neural cascade’ that he says is ‘so tightly integrated and so natural that we barely notice them, if we notice them at all.'” In short, we might not understand what goes into creating or averting the fiscal cliff, but we know it should be avoided. Going down is bad, and staying up is good. The episode got me thinking about similar spatial metaphors and the work they do in our augmented society. One of the more ubiquitous metaphors is “high tech.” Is high tech “good” technology? Or is it high in the same way the Anglican Church uses the word; steeped in conservative traditions and formal code?

What do we mean when we say “high tech?” Usually it has something to do with computers, but really complicated science also seems to fit. We would call nano-scale bioengineering high tech, or maybe pharmaceutical research. High tech is usually not civil engineering (unless we are talking about the highway operations center or “smart” parking), language (even though it is a technology), or carpentry. High tech is a nebulous, contestable term, but its associated imagery is remarkably uniform: blue and white swirls and streaks overlaid with floating sets of numbers, lines, molecules, and circuit boards. The disembodied hands are always white and the globes always show the western hemisphere. Writing your top 10 list of “high tech grills”? Then half of your stock grill image should be a glowing blue microchip. If you were to write a definition of high tech based on these images it would read: “blue-tinted gaseous substance, sometimes luminescent, emitted by ethernet cables that mark the arrival of humungous white people that want to poke continents. (See figure at top of page.)”
 Where did the term “high technology” come from? A Wikipedia contributor, on the article’s talk page, offers this clue: “The band Love released an album called Cybertracks in 1966 with the words “HI-TECH ELECTRONIC MUSIC” on the cover. It’s not definitive, but I mention it in case it helps.” The Oxford English Dictionary cites Agar and Tate’s Who Owns America? as the first instance of the phrase, which is used to describe mass production of goods in factories. Who Owns America? originally published in 1936 was a popular conservative rebuttal to the New Deal reforms instituted by the Roosevelt administration. Anyone that has uttered the words “wealth redistribution” with a healthy dose of sincere disgust has been influenced (indirectly) by this book. Despite the text’s popularity, it seems as though conservative intellectuals were alone in their use of high technology for another three decades.
Where did the term “high technology” come from? A Wikipedia contributor, on the article’s talk page, offers this clue: “The band Love released an album called Cybertracks in 1966 with the words “HI-TECH ELECTRONIC MUSIC” on the cover. It’s not definitive, but I mention it in case it helps.” The Oxford English Dictionary cites Agar and Tate’s Who Owns America? as the first instance of the phrase, which is used to describe mass production of goods in factories. Who Owns America? originally published in 1936 was a popular conservative rebuttal to the New Deal reforms instituted by the Roosevelt administration. Anyone that has uttered the words “wealth redistribution” with a healthy dose of sincere disgust has been influenced (indirectly) by this book. Despite the text’s popularity, it seems as though conservative intellectuals were alone in their use of high technology for another three decades.
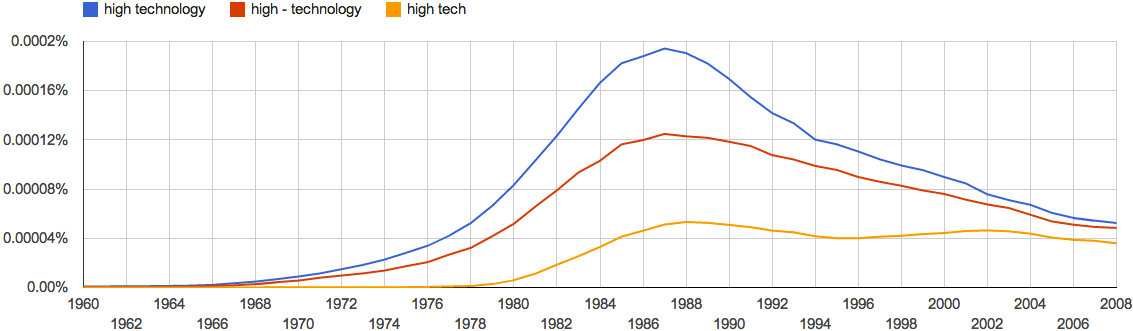
Google Ngram viewer shows the terms “high technology” (with and without a hyphen) and “high tech” coming into widespread usage in the seventies and peaking between the years of 1987 and 1988. Today’s authors use all three versions about as often as authors used “high technology” in 1976.
High tech, while usually used as a positive modifier today (i.e. “High tech gadgets that make your life easier!”) was originally used to describe an unwanted development. For Agar and Tate, High technology is something inaccessible and uncontrollable by the common person. High technology is alienating; a tool of big government to remove political and economic power from private citizens. How can a metaphor effectively convey both good and bad? We might simply write this off as a difference in opinion over complexity and technical organization. Some people like high tech, and some do not. But a metaphor can spread out in different directions. The “neural cascade” described by Lakoff and Johnson can branch out in different, sometimes opposite, directions. Lakoff and Johnson would consider the term “high tech” an example of an orientational metaphor. These are metaphors that make use of our shared embodied experiences (we all experience gravity, for example) to convey a certain idea about one subject’s relationship to an overall system. The authors provide a list of attributes widely associated with “up” in Western contexts:
- Happy (spirits are high)
- Conscious (wake up)
- Health or life (top shape, peak of health)
- Control or force (one has control over something)
- More (production is up)
- Foreseeable future events (upcoming events)
- High status (lofty position)
- Good (things are looking up)
- Virtue (high standards)
- Rational (as opposed to emotional- we rise above our emotions)
It is important to note that the above bulleted list is not a matter of simple word association. These connections are linguistic, but they are also cognitive. By describing something as high tech you are not only associating it with power, and control, you are also reestablishing the social values that embue the object with those attributes. Would if we replaced all instances of high tech with “complex technology” or “controlling technology.” These might be passable descriptors in some instances, but it does not have the cultural cache of high. High tech is a reward, a sign of success, and an upgrade from whatever you had before the high tech gadget came along. The utterance of the metaphor high tech justifies the existence of the object it describes. Low tech solutions are poor, uncontrollable, and provide no control over the forces of nature that they are supposed to tame. High technology is associated with the future and, as Leo Marx has shown, sometimes we mistake new technological achievements for social progress.
This very basic metaphor: high is happy/good/powerful/rational is very different from the more deliberate kinds of metaphors that are used to describe the relationship between two objects. For example, the Master-Slave metaphor found throughout computer science and mechanical engineering has a very specific history and is almost always used to describe a hierarchical relationship within a technical system. Ron Eglash has charted the history of the metaphor and postulates, “the master-slave metaphor is attractive to engineers because its free use ‘proves’ that they inhabit a nonsocial or culture-free realm, which is a matter of professional pride.” Eglash is describing what Haraway would call the “view from nowhere”: the notion that professionals view a problem based on objective criteria and never their own personal background or standpoint. If we were to ask a sample of engineers whether they thought the high tech metaphor was useful, accurate, or desirable, I suspect we would get a bunch of “that’s just what its called.” We would not hear about its connotations to patriarchal concepts of rationality or control.
These connections are, of course, just the beginning to a thought process. The “neural cascade” might encourage us to look at our new gadget in an uncritical way, but we are not inextricably bound to see iPhones as good and weaving looms as bad. By recognizing that the words we use to describe whole categories of technology can subtly influence our decision-making, we can regain control over our own creation. Just as we tend to avoid cliffs, we are also in favor of being happy, healthy, and good. Perhaps the answer is simply to redraw the boundaries around what we call “high tech.” An awesome cross-stitch pattern or an innovative work organization scheme could be high tech. We might desire more control or wish to make a calculated and rational decision, but we would be mistaken to think that a gadget will automatically give it to us.
Follow (well that’s a loaded metaphor!) me on Twitter: @da_banks